Cryptocurrency hardware wallet manufacturer Trezor announced a troubling security breach on January 20th which exposed the personal contact information of nearly 66,000 of its users.
The company stated that unauthorized access to one of its third-party customer support portals had been identified on January 17th, compromising the data of users who had interacted with Trezor’s support team since December 2021.
TLDR
- Trezor suffered a data breach exposing 66,000 users’ contact info to phishing risks
- The breach occurred via unauthorized access to a third-party support portal
- No user funds or Trezor devices were compromised, but contact details were exposed
- At least 41 users have already received phishing emails requesting seed phrases
- Trezor has a history of phishing attacks and security incidents with fake hardware
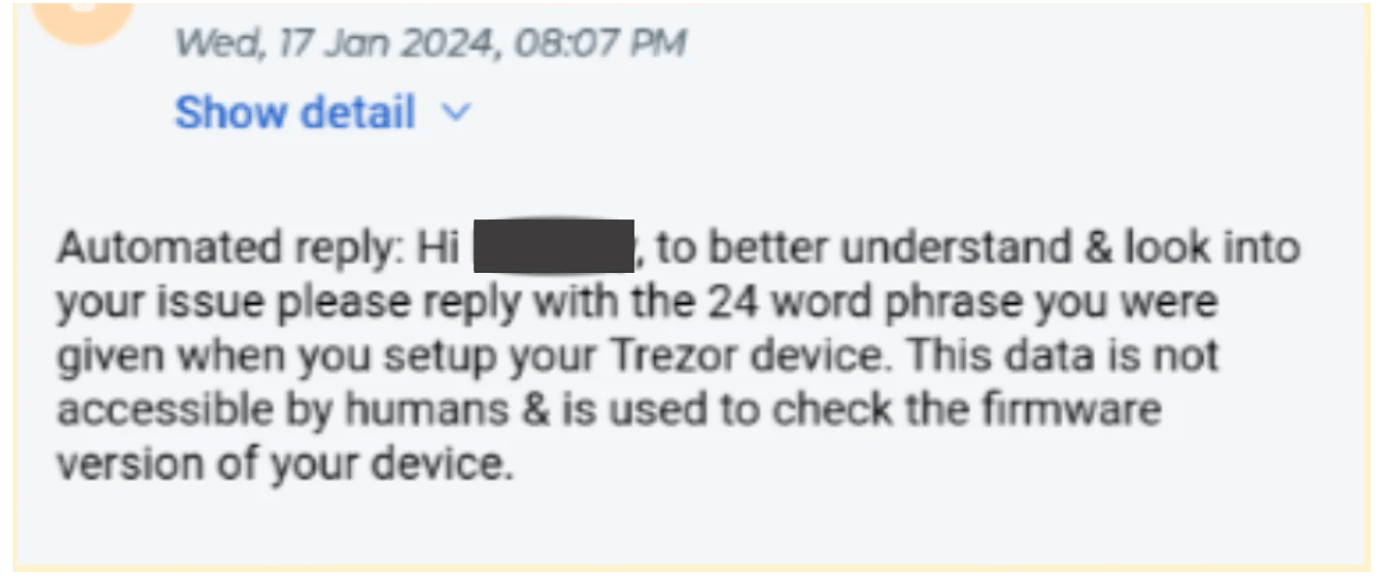
While Trezor confirmed that no user funds were put at risk in the breach, the exposure of email addresses, names, and other contact details poses a critical phishing threat to affected individuals. Trezor was quick to email notifications to all 66,000 impacted users, warning them of potential phishing attempts seeking to steal personal information or cryptocurrency wallet recovery phrases. Indeed, at least 41 users are known to have already received direct phishing emails from the attacker just days after the initial breach.
Beyond those 41 users, 8 more individuals who had signed up for accounts on the same third-party support portal also had their information improperly accessed. Trezor stated that it warned all known recipients of suspicious messages within an hour of detecting the unauthorized activity. Despite this quick response, the contact exposure has sharply increased risks of credential theft, financial fraud, and seed phrase phishing targeting Trezor clients.
The company attempted to reassure affected users that aside from the contact detail disclosure, their Trezor devices remain fully secure, with no assets or recovery phrases actually being accessed in the incident itself. However, Trezor products have been plagued by security issues in the past, including phishing attacks in March 2022 which sought to trick users into entering wallet recovery phrases on fake Trezor sites to enable asset theft.
Other incidents involved attackers distributing convincing counterfeit Trezor hardware devices which were capable of stealing the private keys and crypto holdings of unsuspecting buyers. These previous cases highlight why the contact information breach is so concerning despite funds not being directly impacted — the data exposure enables many future phishing and fraud efforts which Trezor users must now vigilantly guard against.
In an effort to combat these risks in the wake of the support portal compromise, Trezor stated that it has tightened platform security measures, enhanced internal data access policies, and implemented stronger protections around third-party integrations to prevent such an incident from recurring.
The company has also advised all potentially affected individuals to never share wallet recovery information or other sensitive data with any unsolicited contacts, no matter how convincing the communication may appear.
Trezor has promised continued transparency and urgent notifications to clients in the case that any new phishing methods are discovered leveraging the exposed contact records obtained illegally via the customer support database infiltration.
With cryptocurrency thefts exceeding $2 billion in 2022 despite the ongoing market slump, Trezor users have cause for heightened caution and cybersecurity awareness to ensure their digital assets remain protected following this latest security scandal among leading hardware wallet providers.
The long-term impacts of the data breach on client trust, platform usage, and Trezor’s reputation in an increasingly competitive landscape have yet to fully play out.
Source: https://blockonomi.com/trezor-breach-exposes-66000-to-phishing-is-your-crypto-at-risk/