In a targeted exploit, decentralized exchange (DEX) aggregator and liquidity protocol KyberSwap, which serves as the main protocol in the Kyber Network’s liquidity hub, suffered a significant security breach.
On November 23, 2023, KyberSwap was attacked, resulting in the theft of approximately $54.7 million, according to intelligence provided by the SlowMist Security Team. Now, more than seven days after the initial attack, the hacker has issued bold and audacious demands.
Critical Vulnerability In Liquidity Management System
The attack involved a series of meticulously planned steps. The attacker began by borrowing 2000 Wrapped Ether (WETH) through a flash loan from the AAVE protocol.
With 6.8496 WETH, the attacker conducted a swap for frax Ether (frxETH) in the KyberSwap pool, intentionally causing the frxETH price to exceed the range of all liquidity providers’ positions.
Subsequently, the attacker added liquidity of 0.006948 frxETH and 0.1078 WETH within a specified price range. Manipulating the liquidity amount within this range to be 74692747583654757908, the attacker strategically controlled the liquidity to align with their subsequent attack stages.
The attacker then utilized 387.17 WETH to swap for 0.005789 frxETH, significantly increasing the current price value. Finally, the attacker performed a reverse swap, exchanging 0.005868 frxETH for 396.2 WETH at a price slightly higher than the square root Price (sqrtP) of tick 111310.
The attacker profited from the reverse swap by taking advantage of this manipulation, acquiring approximately 9 more WETH than initially exchanged in the forward swap.
According to the SlowMist team, the attack’s root cause was the miscalculation of the required token amounts for exchanges based on current and boundary tick prices.
Due to KyberSwap Elastic’s Reinvestment Curve, the liquidity inadvertently increased due to compounded fees, resulting in a calculated amount larger than expected. This excess liquidity covered the user’s exchange needs, but the actual price had already crossed the boundary tick.
Consequently, KyberSwap failed to update the liquidity, leading to a duplication of liquidity increase during the reverse exchange across the boundary tick. This flaw allowed the attacker to obtain more tokens than initially anticipated.
KyberSwap Must Yield Authority And Assets
In an unexpected turn of events, the hacker issued a second on-chain message on November 30, following an initial message on November 28.
The demands include complete executive control over KyberSwap, temporary full authority and ownership over the governance mechanism (KyberDAO) to enact legislative changes, and surrender of all assets encompassing shares, equity, and tokens.
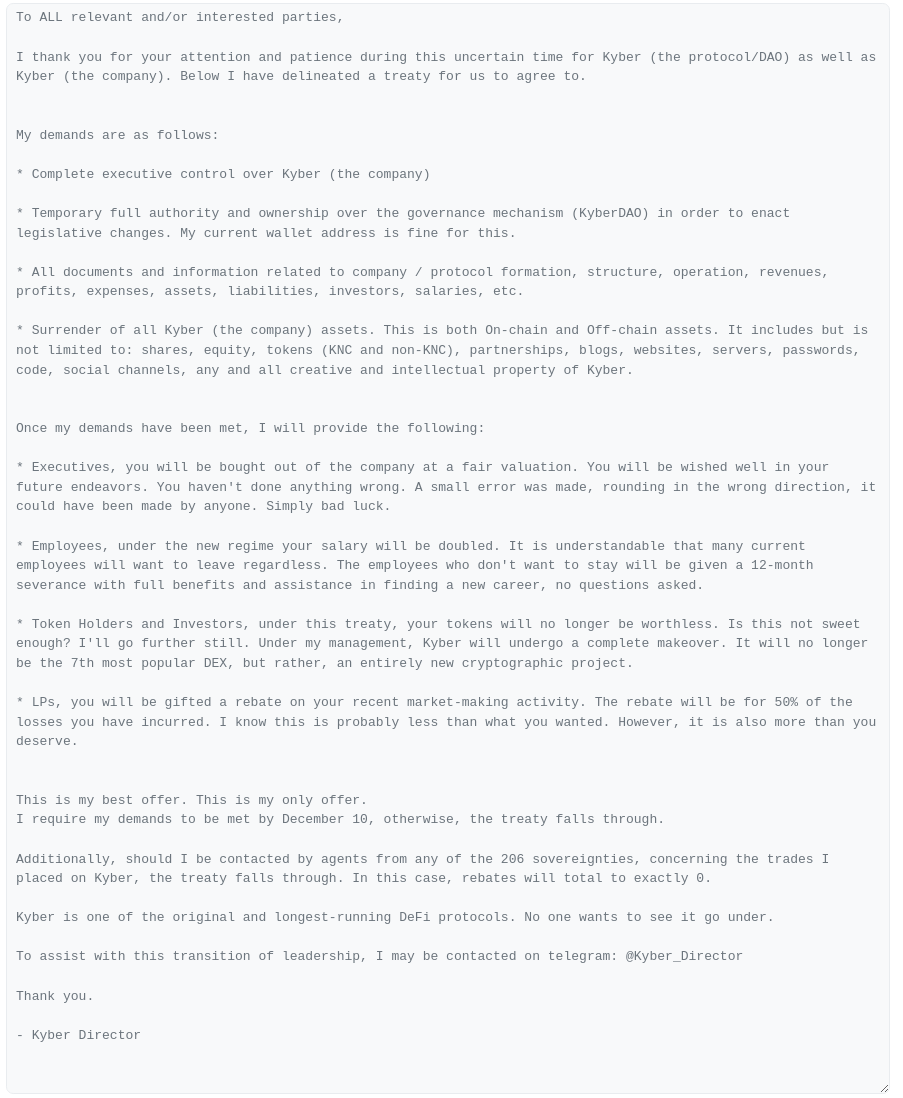
The hacker also promises a buyout of executives at a fair valuation, a doubling of employee salaries under the new regime, and a 12-month severance package with full benefits for employees who choose to leave.
Furthermore, the hacker addresses token holders and investors, assuring them that their tokens will regain value under the proposed treaty. The hacker even pledges to transform Kyber into an entirely new crypto project, surpassing its current ranking as the 7th most popular DEX.
Liquid pool (LP) participants will also receive a rebate covering 50% of their recent market-making losses. The hacker has set a firm deadline of December 10th for his demands to be met, claiming that he can be contacted via Telegram with the handle “@Kyber_Director.”
The next steps for the protocol’s leaders remain uncertain as they grapple with the latest developments and the urgent need to address them within a timeframe of just over 10 days, with no official response to the hacker as of this writing.
Featured image from Shutterstock, chart from TradingView.com
Source: https://bitcoinist.com/kyberswap-hacker-full-control-december-10-deadline/