On May 22, 2025, Cetus Protocol, a leading decentralized exchange on the Sui blockchain, fell victim to a sophisticated smart contract exploit that targeted its Concentrated Liquidity Market Maker (CLMM) pools.
The incident exposed a previously unknown vulnerability within the system’s smart contract logic, resulting in a substantial loss of funds. However, rapid response from the Cetus team and Sui validators helped contain the damage and freeze a significant portion of the stolen assets.
How the Attack Unfolded
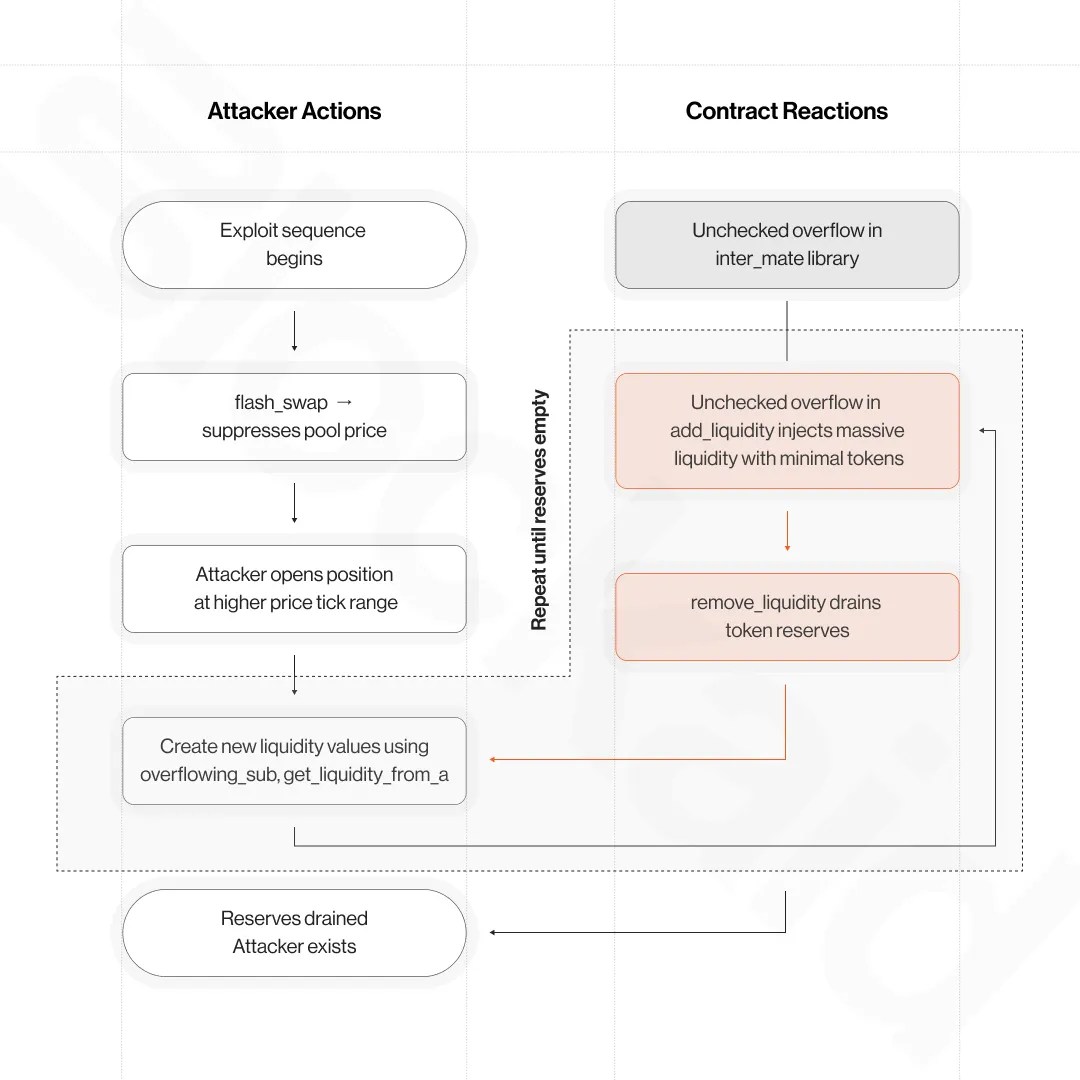
The exploit began when an attacker leveraged a flash swap to momentarily suppress the price of tokens within a CLMM pool. By artificially lowering prices, the attacker was able to open a liquidity position within a higher tick range, a mechanism that sets the boundaries for token pricing in a given pool.
The real vulnerability, however, lay deeper in the contract logic. The attacker manipulated a critical flaw in how the smart contract checked for overflows during liquidity additions. Instead of properly validating input values, the contract allowed the attacker to inject an abnormally large amount of fake liquidity with only minimal token deposits.
After inflating their position, the attacker repeatedly removed this fake liquidity, siphoning actual token reserves out of the pools. This loop was executed several times using precisely crafted values, effectively draining assets by exploiting unchecked calculations and overflow behaviors in the system.
The Root Cause: A Library Miscalculation
At the heart of the exploit was a subtle but critical error in the open-source library used by the CLMM contract. Specifically, the problem originated from a misunderstanding of how left-shift operations should be checked in the checked_shlw method. Instead of validating against the proper boundary (2^192), the flawed implementation incorrectly allowed shifts up to 2^256, enabling the overflow manipulation.
This misconfiguration, though seemingly minor in code, opened the door for devastating consequences when paired with the attacker’s calculated strategy.
Not What the Audits Caught
There was some confusion in the community regarding an older audit report that flagged a MAX_U64 arithmetic issue. Cetus clarified that this previously identified issue was unrelated to the exploit. The MAX_U64 check was a minor optimization recommendation that only triggered transaction reverts in edge cases and had already been addressed in earlier contract updates.
What Happens Now
The Cetus team quickly disabled all affected pools and patched the vulnerable contracts. Working alongside the Sui validator community, they initiated emergency governance procedures to freeze the attacker’s access to the blockchain and prevent further asset movement.
Efforts are now focused on comprehensive re-auditing of all contracts, improving real-time monitoring tools, and designing a recovery plan to compensate affected users. The team is also pursuing legal channels and has issued a white-hat redemption offer to the attacker.
A Hard Lesson — and a Stronger Future
Despite extensive prior audits, Cetus acknowledged that it placed too much confidence in widely-used open-source components without sufficient scrutiny. The incident has reinforced the need for continuous vigilance, layered security, and ecosystem-wide collaboration.
Going forward, Cetus will adopt stricter audit protocols, higher testing standards, and more transparent reporting. The goal is not just to restore user trust, but to set a new standard for resilience in DeFi infrastructure.
This exploit is a reminder that even well-audited systems can have hidden risks. But with rapid action, transparency, and a united community, recovery — and evolution — is not only possible but already underway.
Source
Source: https://coindoo.com/cetus-exploit-everything-you-need-to-know-about-how-it-happened/