- SlowMist security reveals EIP-7702 exploited by high-level theft groups.
- Over 97% authorizations target compromised wallets.
- Significant threat to Ethereum security architecture.
SlowMist security researcher Yu Xian reported on platform X that the Ethereum EIP-7702 is being misused by sophisticated coin theft gangs. Over 97% of EIP-7702 delegations involve unauthorized fund transfers.
This news underscores major vulnerabilities in Ethereum’s mechanism, raising concerns about the network’s susceptibility to sophisticated attacks.
97% of EIP-7702 Delegations Compromised
Yu Xian of SlowMist identified the targeted exploitation of the EIP-7702 mechanism. Sophisticated theft groups leverage compromised keys to facilitate fund transfers, affecting the majority of authorizations. These are not typical phishing attacks but advanced coin theft operations using EIP-7702 loopholes.
“The EIP-7702 mechanism is being manipulated by the highest level coin stealing gang to facilitate automatic transfers of funds from compromised wallets.” — Yu Xian, Security Researcher, SlowMist
Industry reactions underscore the seriousness of the security threat. With SlowMist’s findings public, pressure mounts on Ethereum developers to address the flaws. The crypto community anticipates formal responses to mitigate these challenges as the scale of affected users appears extensive.
Expert Warnings and Potential Regulatory Actions
Did you know? The EIP-7702 mechanism was initially designed to enhance user security but has now become a target for exploitation.
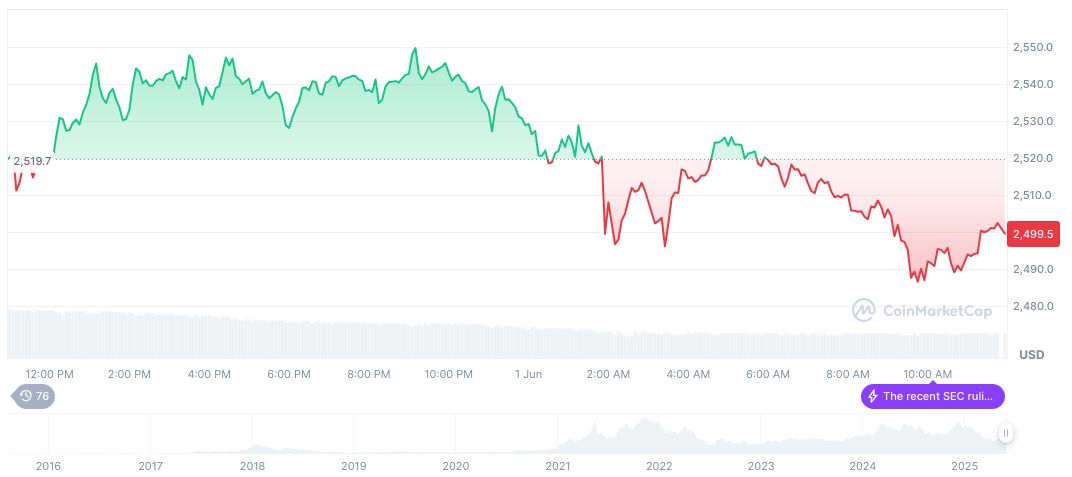
Ethereum (ETH) currently trades at $2,495.98 with a market cap of $301.32 billion, representing 9.16% of the market. Over the last 30 days, ETH has surged by 36.61%, according to CoinMarketCap. The recent incidents, however, question its security standing.
Analysts from Coincu suggest that the EIP-7702 exploitation could prompt regulatory scrutiny. Financial implications are profound, with robust frameworks expected to dampen future exploitation risks. Technological upgrades may be necessary to safeguard users against sophisticated threats.
Source: https://coincu.com/341158-eth-eip-7702-exploitation-theft/